On the 21st October 2014 Microsoft issued Security Advisory 3010060 relating to a flaw in PowerPoint that can allow attackers to gain access to the Windows system.
How is it Transferred?
Microsoft states that the vulnerability could allow remote code execution if a user opens a specially crafted Microsoft Office file that contains an OLE object. Put simply, this means that it’s transferred within PowerPoint files (not add-ins). Fortunately, any attack requires you as the user to provide consent before the malware can run via Windows UAC (User Account Control) which means you can prevent infection.
What Should I Do?
- Be vigilant – ALWAYS air on the side of caution.
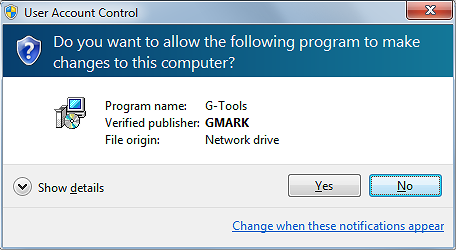
- NEVER accept access when downloading PowerPoint files unless you trust the source 100%. If not sure, check with your IT administrators or contact the owner of the content to ask why UAC is being requested. PowerPoint files (as well as add-ins) can be digitally signed to authenticate their origin. Never allow unsigned code to run on your computer. As an example, this is what a digitally signed application looks like when Windows UAC asks you for consent to run an application:
- Apply the hotfix from Microsoft.
- Make sure your Windows system and Office system is set to update any patches.
[/list]

